Threat modeling : Being ready for the attackers
Threat modeling is an essauntial component of your Information security management system (ISMS). It aims to identify, analyse, plan, communicate, potential threats to protect assets in your network. It is basically, getting into the attackers' head, and deploying effective defences against their Tactics, Tools, and Procedures (TTPs) . Threat modelling requires effective threat intelligence process to protect your organization from emerging cyber security threats.
There are several threat modeling approaches such as PASTA, OCTAVE, VAST, and STRIDE. The particular model applicable for your organization depends on the type of business, assets and threats. Threat modelling is based on your organization's infirmation security objectives and risk assesment outcomes as well as monitoring of indicators of compromises (IOCs). It also need to consider future and potential threats identified by your threat intelligence activities.
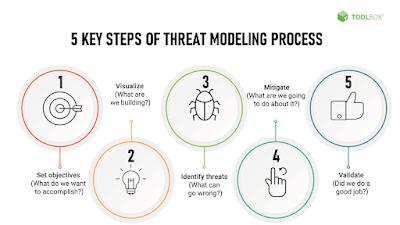
The generic steps of threat modelling recommended by are as follows:
- Assessment Scope: identify assets potential for the threat.
- Threat Agents and Attacks: Identify the groups of adverseries. This include insiders and outsiders, performing both accidental mistakes, malicious attacks leading to data leaks or other compromises.
- Identify exploitable vulnerabilities: Analyse potential vulnerabilities conducting, vulnerability scanning and penintration tests.
- Prioritized identified risks: Prioritization is essential in threat modeling. Asses your risks with likelyhood of occurence and impact factors to determine an overall risk.
- Identify the Countermeasures: These measures are technical, physical and administrative controls identified through your risk management process.
- Develop a plans to reduce threats: Create a plan to implement identified controls to reduce the risk to acceptable levels.
- Implement Controls : Implement the identified controls, train your staff, monitor and measure effectiveness of controls using defined Key Performance Indicators (KPI)
Threat modeling should cover every possible entry point to your network, interfaces to applications, internal systems, cloud systems, Internet of Things (IoT) devices, and exposed business processes.
A threat model typically includes:
- Information assets used by business functions
- KNOWN threat landscape for each asset
- Types of adverseries to be modeled
- Tactics, Tools and Procedures (TTPs) used by adverseries
- Potential threats and known Vulnerabilities
- Means of mitigation or security controls
- A way of validating the model by testing of vulnerabilities
- Means of monitoring, verification and measuring of controls
In abstract, threat modeling is a process to capture, organize, analyze, and prioritize all threats to information assets in organization, to apply necessary security controls for the mitigation of threats to reduce risk levels, and monitor their effectiveness.
Threat Modeling is a cyclic process, which becomes more and more granular throughout it's lifecycle. It gets inputs from threat intelligence of new attack vectors, organization changes, and IoCs which require identification, analysis and addressing of threats.
The threat model should be updated when:
For applications:
- A new feature is released
- Security incident occurs
- Architectural or infrastructure changes
- When operating environment changes
For Networks :
- When network configurations changes
- When networks expands or infratructure changes
- When interfearing with another network (mergers)
Threat modelling is a critical function to ensure information security of your organization. It is an ongoing process sensitive to business, infrastructure and environmental changes. Threat modelling should be based on continues risk assesment and threat intelligence.
Niranjan Meegammana



Comments
Post a Comment