Risk-Based Vulnerability Management: An Automated Remediation to manage Risks
Vulnerability management is a proactive process that is critical to endpoint security. It is aimed to mitigate vulnerability before it leads to a breach.
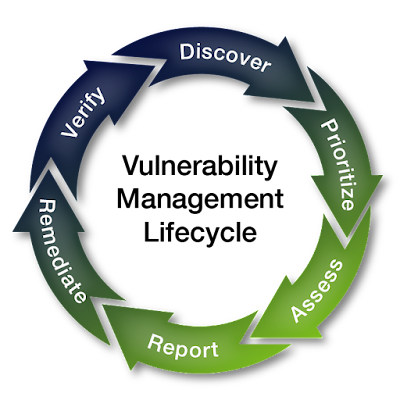
Vulnerability management is a cyclic process, which identifies information assets, then correlates them to a continually updated vulnerability database to identify potential threats, misconfigurations, and vulnerabilities. It also validates the potential impact and probability of various risk factors created by vulnerabilities to respond to serious threats early.
The Forrester Global Security Survey, states that "49% of organizations have suffered one or more breaches in the past year", where software vulnerabilities are the largest. A single vulnerability can help an attacker intrude and steal data. The ever-growing new security holes every day, with most of them having exploits available, highlight the importance of vulnerability management in organization security strategies.
The Center for Internet Security (CIS) defines18 Critical Security Controls for security implementation.
1: Inventory and Control of Enterprise Assets
2: Inventory and Control of Software Assets
3: Data Protection
4: Secure Configuration of Enterprise Assets and Software
5: Account Management
6: Access Control Management
7: Continuous Vulnerability Management
8: Audit Log Management
9: Email and Web Browser Protections
10: Malware Defenses
11: Data Recovery
12: Network Infrastructure Management
13: Network Monitoring and Defense
14: Security Awareness and Skills Training
15: Service Provider Management
16: Application Software Security
17: Incident Response Management
18: Penetration Testing
There are too many vulnerabilities to track manually. They all do not pose an equal risk. Tracking multiple vulnerabilities across thousands of assets in a distributed network is a daunting task. The window between disclosure of vulnerabilities and their exploits are shrinking, hence remediation needs to be swift.
The vulnerability management workflow can be automated with, many tools that offer to patch
When a threat actor uses a vulnerability to intrude into the network, any misconfigurations will help laterally move and exploit other hosts in the network. This requires defense-in-depth strategies to minimize the attack surface.
Although patching the affected machines with vendor-published patches is an option, having a fail-safe strategy is essential for zero-day vulnerabilities and for software ended life.
In vulnerability management, you can only fix what you can see, hence security personnel need to know about the threats and vulnerabilities in their network at all times. This is where Vulnerability Management software steps in.
Vulnerability Management software uses client-server architecture, has a database which is updated by synchronizing with external vulnerability databases. It leverages agent technology, scans servers, databases, laptops, desktops, and virtual machines in the network and cloud systems at predetermined intervals to help with automatic patch management.
It probes operating systems, open ports, installed software, user accounts, file system structure, and system configurations for threats and vulnerabilities and recommends appropriate remediation. It downloads patches from vendor sites, stores in a central patch store, and replicated to endpoints to conserve bandwidth. It also provides a web console to monitor your security posture and carry out tasks anywhere.
Further it prioritizes vulnerabilities to ascertain priority, urgency, and impact. Keep a history of vulnerabilities found in your network. It helps establish a secure foundation with security configuration management, audit firewalls, and antivirus, and prevent brute-force attempts with secure logon policies. SonarQube for Static Application security testing (SAST), and OpenVAS helps network vulnerability management. Vulnerability Manager Plus is a comprehensive commercial tool.
Vulnerability Management Tools
https://heimdalsecurity.com/blog/open-source-vulnerability-management-tools/



Comments
Post a Comment